Now, more than ever, the Internet and the use of technology has taken over more aspects of our lives and integrated itself into our daily fabric. Banking, for example, can now be done fully online with the bank not having an actual building from which to operate from. This can benefit you with lower or no fees and higher saving rates, as the bank doesn’t need to spend money on the expense of leasing an office space, nor the expenses that bring along with it.

With many or all of our financial transactions taking place online or in an automated fashion, we need to be just as diligent as we were walking into and out of the bank with actual cash-in-hand. I would even say more diligent because there are threats out there that you are likely not even aware of. Let’s examine 14 ways that you can be more diligent and protect your finances online, both active and inactive protective methods of online security.
Table of Contents
Keep Your Computer(s) or Phone(s) Updated
All computer systems in use have a method for updating the operating system of the computer. The operating systems used in most of today’s computer systems are Microsoft Windows, Apple MacOS, Google ChromeOS, and Linux. Smartphones also have operating systems to be updated for protection, such as Android, Google, iPhone, and others. It is best to set the computer or smartphone up to perform automatic updates so that it can always have the most recent updates.
When a computer system becomes out of date by not being updated, vulnerabilities can be exposed. As the vulnerabilities become known, your computer can become a target as you have not taken the steps to protect the computer, which can lead to you being the victim of the vulnerability through a hack or a virus or even ransomware. If you keep financial information on your computer, that data can be exposed as well.
Here are the links to the manufacturers’ website instructions for updates. As there are many distros (brands) of Linux available, I’ve only listed the most common below. If you use something else, simply Google the term “<linux distro> automatic updates” (replacing <linux distro> with your specific Linux distro used).
Use Strong Antivirus Protection
Updating the operating systems of your various devices (computers and/or smartphones) will protect them from known vulnerabilities. There are other methods by which a device can be compromised as well. Threats can come in through your email system (this will be covered shortly), through other programs you install, or from online security lapses that have to do with the way in which the device is configured.
To protect against these threats you must use a strong antivirus program. The antivirus program is used to prevent, detect, and remove viruses on the device. The antivirus program runs at all times on the computer, being constantly vigilant. The best antivirus programs are also discrete, meaning that you hardly know they are there most of the time and they don’t require a ton of resources (CPU time and memory) to be effective. Antivirus programs also integrate themselves into the Internet browser you use to protect you while browsing online. I personally use Vipre for my own computer as well as those of my family. I highly recommend the Vipre antivirus solution.
Use Strong and Unique Passwords
Now that we’ve discussed the ways to protect your computers and smartphones, let’s look at one of the most common area that lead to an online compromise: passwords.
We all need to use passwords for practically every relational interaction on the Internet or online. Our bank requires us to authenticate, software sites that we are members of requiring us to authenticate, social media sites that we are members of requiring us to authenticate, and the list goes on and on.
The best passwords are super long and have a variety of letters (both uppercase and lowercase), numbers, and special characters (such as !@#$%). The problem with using these types of passwords is that they are very hard to remember. As a result, we don’t typically use them, or if we do, it is only one and we use that one for everything. The passwords you use online need to be both strong and unique. Each password you use needs to be different from the other ones you use. But how are you going to remember all of these strong and unique passwords?
This is where a Password Management solution comes into play. In my many years of working with computer systems, both personally and professionally, I’ve worked with many password management solutions. There are ones built into the browsers you use and there may be ones built into the operating systems you use. The best Password Management solutions are platform-agnostic, meaning they will work on Windows, Mac, Android, iPhone, etc. I highly recommend NordPass password management solution. My family uses NordPass and we love it.
Use Multi-Factor/Two-Factor Authentication (MFA/2FA)
In addition to using a password to access resources online, you can now enable Two-Factor Authentication (2FA) and/or Multi-Factor Authentication (MFA) on some sites. This is becoming a standard in online security so more and more online resources have the option and some are even starting to require it.
Two-Factor Authentication
2FA adds an additional layer of security to the online resource. It does this by requiring a second credential to be entered before you gain access. Without the second credential access to the online resource is impossible. The typical way that the second credential is provided to you is through an application or through an SMS text message with a temporary code to use at the time of entry.
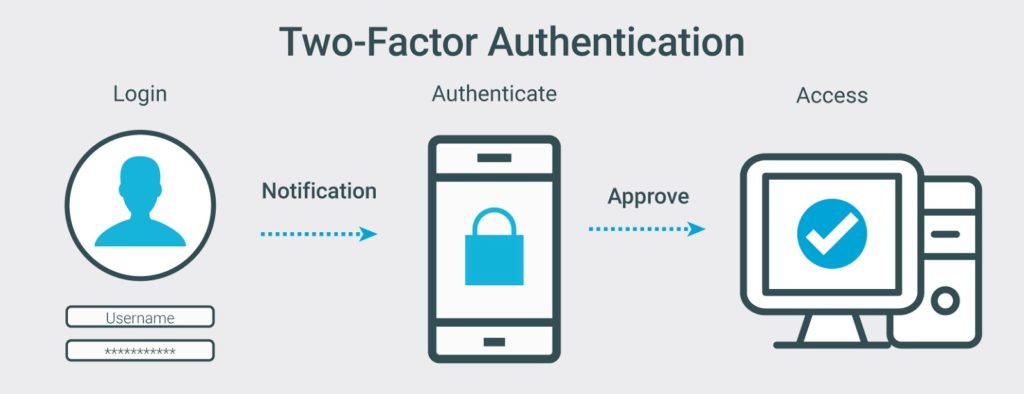
Multi-Factor Authentication
MFA requires at least two additional pieces of information to prove identity, not just one additional like 2FA. Each piece of information comes from a different category. You must be able to pass all roadblocks in order to gain access to the online resource. The additional pieces of information, or criteria, can come from multiple places, such as something you know, something you have, and something you are. The “something you know” can be a PIN or passphrase previously established. The “something you have” can be a smartphone to receive an SMS text with a temporary code. Finally, the “something you are” can be your fingerprint. As you can see, with all of these criteria to verify, the odds of someone other than you getting past the roadblocks is almost impossible.
Multi-Factor Authentication

Beware of Suspicious Emails (Phishing)
Malicious attacks that come in via email are called Phishing. Phishing is a crime where the target(s) are contacted by email by someone posing as a legitimate user or organization to lure you into providing sensitive information such as banking, credit card details, or a password. The perpetrator then uses this information to access your accounts for a financial loss to you. This can also result in identity theft.
There are some common things that phishing emails have. You can use these to identify phishing emails.
Too Good To Be True
The content or request is too good to be true. You won a lottery, a new car, or other lavish prizes. Don’t click any links contained in the email.
Urgency or Act Now
The message belays a sense of urgency. Act now or within a certain time frame or the offer will expire.
Unexpected Attachments
If you receive an email containing an attachment you were not expecting. Don’t open it without further investigation. Call the sender to validate legitimacy.
Verify the Legitimacy of the Email
The email comes from an unknown sender. If anything seems out of the ordinary or unexpected, be suspicious until the sender is validated. Hover over the return address hyperlink to see if it goes back to where it appears to have come from.
Look for Obvious Errors
If the email is pretending to be from an institution, carefully inspect the pictures/logos. Is that what the Bank of America logo really looks like? Again, verify authenticity. Are common words misspelled?
Don’t Click on Links Immediately
False hyperlinks are a big tell of phishing emails. When you hover your cursor over a hyperlink in an email, you will be shown the true destination of that hyperlink (you are informed via a pop-up or by seeing the true link at the bottom of the screen. If they don’t match, then the email is phishing.

Be Careful on Public Networks (VPN solutions)
When using networks that are provided for the public’s use, such as a library network or a coffee house, such as Starbuck’s, know that others can read the data which you are sending and receiving. This is known as packet sniffing. If you are on a public network and checking online financial institutions, the details for that financial institution such as your username and password may be captured via packet sniffing.
You can protect yourself while in public by using a VPN solution. A VPN (Virtual Private Network) solution creates an encrypted tunnel between your device and the destination or secure network. Encrypted data is concealed by converting it into protected code that then requires the encryption key to make the contents readable. All the data that transverses the VPN is encrypted and thus unreadable if captured. I highly recommend NordVPN for a VPN solution.
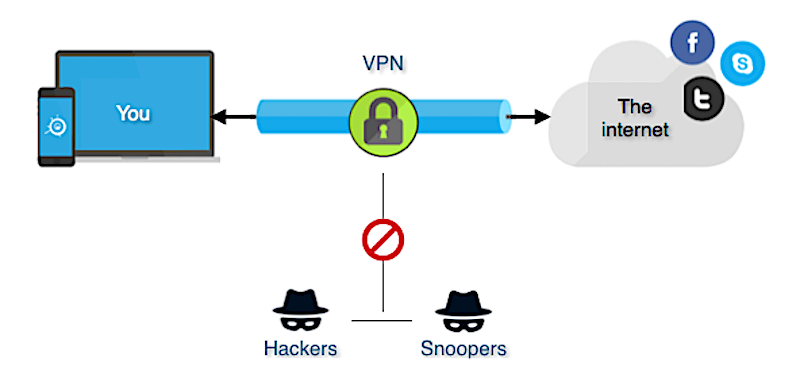
Do you Online Banking from home
As stated in the previous section, it is much safer to perform any online financial transaction from home rather than a public network without the use of a VPN solution. Typically home networks are far safer than public networks as you usually know who’s on your home network and what they are doing. Be sure to make your password to access your home network as strong as possible (see the section for Using Strong and Unique Passwords above).
Suspicious Website Check
Be wary of suspicious websites. Your antivirus solution will help to protect you from connecting them, usually by adding icons next to your search results to indicate that the website is legit or suspicious. You can also check by hovering over the hyperlink to the website to check where you are really going to be set to (see the section for Verify the Legitimacy of the Email above).
Actively Check Your Credit Report and Bank Statements
You should regularly check your credit report (at least once per year) and review your bank/credit card statements. I review my bank/credit card statements when I reconcile those accounts once a month. I also usually do it a couple of more times each month as I’m entering transactions. You are entitled to one free credit report each year from each of the credit reporting agencies: Experian, TransUnion, and Equifax.
Sign Up for Credit Monitoring
In addition to checking your credit report annually, I also recommend that you sign up for a credit monitoring service. Credit Karma and Experian are both highly regarded solutions in the industry.
Lockdown Your Credit
One safeguard that we use is to lock our credit so that credit accounts cannot be opened in our names without our knowing. This can be done manually at each of the three credit reporting agencies (Experian, TransUnion, and Equifax). It can also be done automatically as a service such as Experian’s IdentityWorks.
Don’t Put Personal Info on Social Networks
Typically when you set up an online financial account, not only are you required to set up a username and password, but you are also asked to answer some security questions that will be used to identify you should you need to reset your credentials in the future. These questions are all pretty much the same: birthdate, mother’s maiden name, first car, favorite book, childhood best friend, etc.

With a little digging, this information (some, most, or all) can be found on social networks that you subscribe to. Facebook is an excellent target to find these details, especially if your profile is public. You can protect yourself by making your profile private, or better yet not putting these details out there, to begin with. Is another like on your birthday worth the risk of having your identity stolen? Even making your profile private is no guarantee of online security as there are ways to get around the privacy if you are determined enough.
Also, sites like Facebook and other social networks are prime targets for a massive hack, where millions of users’ details are acquired. In September of 2018, Facebook reported that it was compromised by a hack that compromised the personal information of 50 million users. That information is then used, either by the hackers or sold on the Dark Web, to perform identity theft. Are you sure that you weren’t one of the 50 million compromised users?
Shred Documents Before Disposing of Them
This last recommendation might not seem like it has anything to do with your online security, but like social media, personal information can be gleaned from what you throw away. Hackers can also take your trash and sift through it to find the details they need to create financial havoc for you online. Getting a simple paper shredder can take care of this security hole.
Backups
With cloud storage being so inexpensive, there is almost no reason not to backup your data in the cloud. People have no problems with buying insurance for their car, their home, and themselves, but when it comes to backing up our data, there is a disconnect. With malicious software such as Ransomware becoming more and more prevalent, having a solid backup of your computer’s data is the only way that you be fully protected. I use BackBlaze for my own computer at home to backup all of my data. You will discover it to be one of the most Financially Grounded solutions to be found. I’ve used them for years, both personally and professionally and I can’t recommend them more.
Conclusion
The information provided here are recommendations that you can take to better secure yourself online and protect your finances. Doing just one will make you safer than you are right now. Each of these that you implement will make you that much safer. In the technology industry, this is known as hardening, as you are making it harder for hackers to get your information.
Another thing to realize is in this ever-changing world we find ourselves in, you can’t simply do this much and forget it. As new technology becomes commonplace and new methods for doing things become the norm, you must always work to be ahead of the hackers. Implementing these securities allows you to worry about other things in your life and focus your energies elsewhere. A little less anxiety is good for the soul I think.
Related Topics
Check out my posts Savings: Why Is It Important?, What You Need to Know About Debt, 6 Excellent Reasons to Invest for the Long Term, and 7+ Forms of Income You Need to Know to see where you might want to apply these recommendations.
Thank you,
Kevin Krhovjak



Hello Mr. Krhovak, I am really impressed with your new Blog. I will follow you and encourage others to do as well. Any way that I can help increase your followers, I will. I wish you good luck!!!
Have a Blessed and Safe Week,
Take Care, Desi Steffen
Mrs. Steffen, so glad to hear from you. Thank you for the compliment. Please let your friends know of this blog as I believe that my knowledge and experience can benefit others.
Sincerely, Kevin Krhovjak
Pingback: 7+ Forms of Income You Need to Know - Financially Grounded
Pingback: Savings: Why Is It Important? - Financially Grounded
Heya i am for the primary time here. I found this board and I find It truly helpful & it helped me out a lot. I am hoping to present one thing again and help others like you aided me.